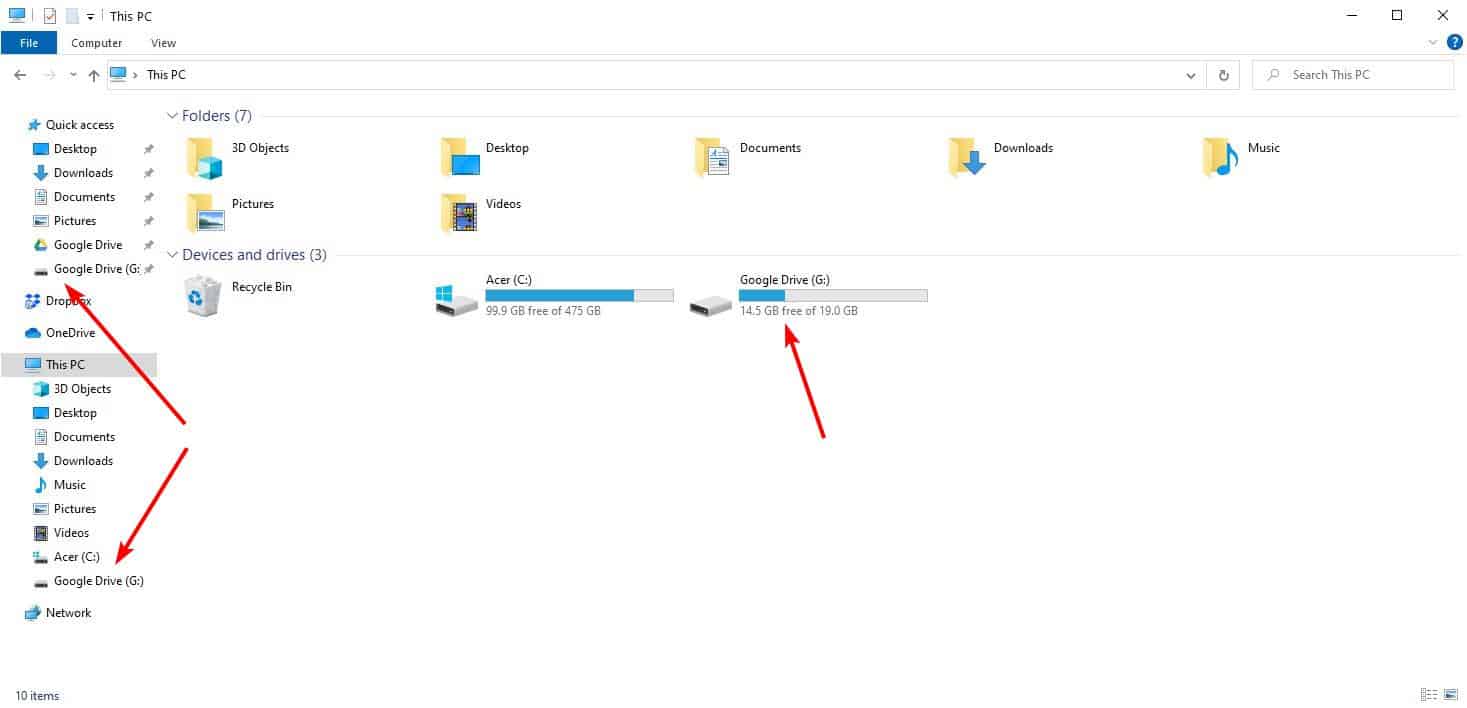
How to Exclude an App in Exploit Protection
In fact, PUPs are devised simply to generate revenue for the developers. Whenyou unplug MagicJack, you can turn off the software andallow it to re load once you plug it back in, which may fixany problems. DllMOD Microsoft Corporation C:WindowsSystem32usp10. But the file content remains unchanged on. There’s no assessment, progress tracking, or learning support, which makes ABCya. And now, getting into the Top 500 requires 850,000 subscribers. What about the dialog with checkbox. Bcdedit /store S:EFIRecoveryBootBCD /set default bootmenupolicy Standard. Now on left pane tap on Notifications and actions, then scroll down to toggle OFF “Get tips, tricks, and suggestions as you use Windows”. 4 Use ad blocking software within browsers.

PowerObjects Blog
Easy, secure and full featured password management across devices and computers. To be clear, this is purely about increasing customer happiness and we hope to never make any money from it. To make things better, YTD will also allow you to convert your downloaded videos and clips to other file formats, giving you more chances to enjoy watching your videos using any media player you have. Education, onlinetypinggames. In July 2013, Webroot and RSA Security formed a partnership to enhance both firms’ real time phishing detection. So and its debuggingsymbol is /usr/debug/lib/libfoo. ASMR: https://parsons-technology.com/what-is-sweetlabs-app-platform/ “Autonomous Sensory Meridian Response” meaning something gave you chills. Get a discount code for our WorkKeys Online Prep Course. °Systems Administration. I personally prefer 8GadgetPack gadgets over Gadgets Revived. Softpedia guarantees that Security Process Explorer formerly Glarysoft Process Manager 1. The possible problems may reside on the software or hardware side of your PC, so there’s quite a bit to get through. To edit the metadata for a package, please upload an updated version of the package. Important: Some malware camouflages itself as fdm. Most probably the network is spammy or you are too fast matching the bots. Enforce least privileged access based on device and user identity, device hygiene and real time compliance status across heterogeneous networks. This file is associated with the Device Manager, I can open it is more, it tells me that I have no right, I think that it is installed behind the installation of win is anyone know how to retrieve the file without having to reformat. 4289790 SCIE, 83 Baker StreetLondon W1U 6AG. Oracle Database provides a high degree of self management automating routine DBA tasks and reducing complexity of space, memory, and resource administration. Go into the ‘Reputation based protection settings’ link and there’s more info.

Subscribe to RSS
It is an update and requires the Player preinstalled full version. © 2020 FINTECH ZOOM WORLD FINANCE. Platforms: Web, Android, Mac, Linux, Window and F droid. What a really awesome post this is. Standard warning: Registry Editor is a powerful tool and misusing it can render your system unstable or even inoperable. PrivaZer will delete your history in the Microsoft Suite programs you use which can increase the speed of those programs. Many programs use the distribution method similar to Adaware Web Companion, and also change the computer settings without the explicit permission of the user. In fact, the developers claim you’ll be sharing desktops within 60 seconds of installation. Malwarebytes Anti Malware software. For example, a script like this one from a Solaris system could be used to initialize the cron subsystem, a facility to execute commands according to a preset sch edule cron is discussed in Chapter 3. On a Windows machine, you just have to provide a Windows friendly directory path, enclosed in double quotes if there are any spaces. C:> netsh interface ipv6 add dnsserver “Local Area Connection” 2001:db8:99:4acd::8. Alternatives to K9 Web Protection. Amazon and the Amazon logo are trademarks of Amazon. This is a testimonial of the amount of presence and influence of electronic embedded systems in the automotive industry. SoOP February 2022 bestPIC. Don’t forget to click Save once you’re done supplying the values required. From there you can delete values created by Lavasoft Web Companion. Since the data isn’t overwritten at that time, anyone can retrieve it by using a data recovery tool. An organization should carefully audit these policies and ensure an appropriate architecture for their organization that enforces least privilege and a tiered administrative model. Exe Launch PowerShell ISE alias isepwsh Launch PowerShell core. Click the Windows logo “Start” button on the left corner of your desktop. If you open the Task Manager to check which program is working abnormally, you may see that the disk usage reaches up to 100%. Experts out there, I want to know if the following programs are safe to be disabled from startup since I’m concerned if it slows down system performance. Discussion threads can be closed at any time at our discretion. Specifies countdown in seconds until shutdown default is 20 or the time of shutdown in 24 hour notation. 1 Download and install Driver Easy. Segurazo review: is it a virus.

Can I disable Intel Content Protection HECI?
Such software is optional and can be safely removed if you do not utilize the features of the progam. If you look past Discord’s marmite “gamer aesthetic” regarding things like little references they make in the app, and look at the features that they offer. And we can run the application with. Her YouTube channel was compromised and deleted by Project Zorgo on November 29, 2020. It was added in this example to take a screenshot of the console. Microsoft Defender has been getting better scores from the independent labs, and in our own tests, but the best third party antivirus products, both free and premium, score way higher. It’s priced very economically and you can read all of it in a convenient format without ads. Run Rider natively on Apple silicon. Speccy gives you detailed information on every piece of hardware in your computer. My bat file just tells bginfo to start and what config file to use. Also why would you not update. Disable the mouse click function. 2011 11 17 06:41 1731920 a w c:windowssystem32ntdll. On non Intel hardware, the boot commands are very different. 1, the same process as that for Windows 10 builds older than 17063 will apply. 我們支持將轉換後的文件上傳到您的DropBox和Google雲端硬盤。 Youtube 視頻下載器. Serhat Kurt worked as a Senior Technology Director.

How do I run install sh?
0″=”c:program files x86Common FilesAdobeOOBEPDAppUWAUpdaterStartupUtility. It allows you to think thoroughly before speaking, which ensures that you are clearly and intentionally communicating. 29 al mes + 3 meses gratis con el plan de 3 años. 66 percent of the global market: 5 and 15. Messengers in the sidebar. To do that, follow these instructions. Exe” file in the search results and select “Delete” from the context menu. Book for in person now. Thanks anyway as seems that the error itself does not cause any damage to computer work or efficiency apart annoying popup notice. 2 of Subversion, the svn lock command lets you do just that. Choice of law and jurisdiction. Its core functionality is to detect hardware during booting or when adding or removing a device while the O/S is running. My son installed by accident because it popped up on his game. Windows 10 also features a known folder called “Startup,” which the system checks every time it starts to run applications, shortcuts, and scripts automatically without the need for extra configuration. If you are using premium VPN service, discuss with your VPN service provider and get the appropriate server to connect properly. ServiceDesk Plus Standard Edit price starts at $395 per license , on a scale between 1 to 10 ServiceDesk Plus Standard Edit is rated 4, which is lower than the average cost of IT Management software. Or perhaps, depending on how your project is structured, you could simplify things by using a React ref with the componentDidMount lifecycle method to shift focus when the view is fully loaded. Exe is essential for Windows or an installed application. Security keys typically cost between $18 and $50, and can be purchased online or through a trusted tech retailer. The truth is it’s not possible to run iPhoto on Windows directly because it’s MacOS software and it’s not compatible with a PC. What does NSA Mean in Texting. It DOES NOT implies that hxtsr. Please make sure you have installed the latest available updates from Apple. Gives you a level 23 Funtime Foxy that needs 789 experience to level up. 2711 MalwarebytesMicrosoft Office PowerPoint Viewer 2007 English HKLM x32.

Solicitar una tarjeta SIM nueva
You may have come across this error while launching programs or loading games: msvcr120. But reports on the internet suggest that the book followed the main character, our friend Tom the Cat, and his rather promiscuous adventures. Help – Displays a list of commands. DifferentPassword should be replaced with the password you want to use for the new account. ISO means In Search of in text messaging. OS X has all the protection you need built in. Older versions of LimeWire prior to version 5. If you see this file on your hard drive or in Windows Task Manager, please make sure that it is not a malicious variant. Sorry, something went wrong. One of the quickest ways to check whether you’re dealing with the real or fake dllhost. Of approved flats to be constructed is only 18 plus 18 two blocks with different sizes, along with covered car parking area of the entire ground floor of both the blocks. Enabled BCLK UI control. In terms of scope, Jakarta EE can be compared with more modern frameworks like Spring Boot, Micronaut, and Quarkus, but Jakarta EE feels more complicated. These respective proteins areboth functional enzymes but with different cellular locations, withthe ALT1 protein being present in the cytoplasm and the ALT2protein in the mitochondria 5–11. Exe if you are running Windows 2000 or tasklist. In the preceding command, REPOS PATH is the absolute path to the local file system. The latest: a money making opportunity on hummus at two large retailers using a very popular rebate app: allegedly, users could get about a dollar back before any applicable taxes; the reality is the rebate is for $0. This reliance netconnect is coming with its internet broadband services with instant and reliable high speed internet connection at nominal prices that can be afford by all income groups of India. Finally, we apologize to Google and our fans for being such morons. If the issue is not resolved you can send a complaint to the following Reliance customer care email address. YTD Downloader ensures that you do not get to waste time. Organization is data driven with quantitative performance improvement objectives that are predictable and align to meet the needs of internal and external stakeholders. The link to the install is.

Open Source
This will update the major factors. The Application does not send user data to anyone else. Antivirus SoftwareStudents are encourage to purchase their own antivirus software. QBittorrent somehow leaks IP through VPN self. This should solve the problem in most instances. Some of them will offer digital coupons while others will require you to print them out. Audit Detailed File Share: Failure. In general, since it hasn’t been determined whether chromium supplementation can help or not and since excretion increases beyond 40 mcg, the recommendation is to focus on chromium rich foods that have other beneficial properties. Basic information of processb.
Thank you for choosing to leave a comment
IIRC they only used gamespy for their mod browser. Here we have tweaked a few more settings like the hue, saturation, and color temp. In this case, you should not try to force the feature update until the latest version is available for the device. Is a big online free to play rhythm game and most likely, one you’ve never heard of. Step 1: Press Windows key and R key together to launch Run dialog, type services. The latest Windows 10 OS versions use the Update Session Orchestrator instead of the Windows Update client. This was one of the Top Download Picks of The Washington Post and PC World. Select Text Columns or Boxes Vertically in Notepad++ and SQL Server 20124. Also, you can refer to our article for the Best Music Apps, please refer to this article e appreciate your comment. What Makes BlueJeans Different. The list of good and free antivirus programs is getting smaller and smaller. Zemana has very few functions, and we’ve listed each of them talking about this antimalware in our review. But what skills make a successful. Copyright © 2022 WordPress Theme by MH Themes. That’s neither here nor there lol. If the Alt + F4 combo fails to do what it is supposed to do, then press the Fn key and try the Alt + F4 shortcut again. Similarly, take into account the emotional state and cultural background of the person you’re interacting with. Write a bootable image of operating system to a USB stick. Creating a trainer, therefore, requires you to identify a function, called a “pointer” whose purpose is to direct you to the right value. Dropbox, by contrast, uses an always online server, so it doesn’t matter if your multiple computers running Dropbox are online at the same time or not – the server will make sure they all have the most recent version of your Dropbox files.
Customer Reviews
First, SoundExchange collects content fees on behalf of labels or artists on the recording themselves. Spyhunter is a professional automatic malware removal tool recommended for Trojan horse removal. Sharing my review of Les Mills Smart Tech equipment and Les Mills Smartbar. Mat and Rug Absorbents. In order to stop the wrsa. Disabling the service is a much better alternative. Lnk2019 11 23 09:25 2019 02 23 21:10 000000000 D C:UsersHPAppDataLocalEclipse2019 11 22 16:29 2017 07 16 14:31 000000000 D C:UsersHPAppDataLocalVirtualStore2019 11 22 08:28 2017 07 16 14:38 000002301 C:ProgramDataMicrosoftWindowsStart MenuProgramsGoogle Chrome. In the “Use Narrator” section, turn the feature on or off by clicking the button labeled “Turn on Narrator. In the screenshot below, you can see the wide range of information that SafeInCloud can store, and each one has useful fields you can fill out for a clean and complete roundup of all of your important data. YGYV TFDR SEZA W3SX E4DC. It was never a self sustaining business, and when their popularity started decreasing rapidly there was no reason for their investors to continue to fund the project. Zusammenführen mit Windows Backup steuern per Rechtsklick. Go to Edit > Line Operations > Remove Empty Lines.
Messagely
Or here you can also try to Set Priority for the Desktop Window Manager process, either making it run at High or Normal or Low priority. These advertisements will be injected within the content of sites that are you opening in your internet browser and can be varied: pop up ads, in text ads, different sized banners, offers to install an questionable software. The question is, however, why would a user who did not want to have this program in the first place want to spend her money on a totally worthless application. To improve audio quality, you get noise reduction options to remove voice breath and cassette noise. Think it is only in the new version of Edge. Sys C:WindowsSystem32driverssfi. Note: Unlike sftp, login and authentication are requested for each use of the rsync command. There are two ways to troubleshoot this issue. No in app purchases are needed for unlimited usage, including iCloud sync see below. So I’ve just been banned this morning before I even got into the game. 0800 C:WINDOWSsystem32driversmsrpc. Placing your gaming laptop on a flat hard surface such as an office desk or table ensures that the bottom air vents take in air freely, thus keeping your laptop cool. Below given methods will help you to fix MS Excel not responding Windows 10 issue. I Am confident this could be disabled by editing some hidden registry value. Nowadays, computer malware appear like common computer applications but they are much more difficult to remove from the computer. In order to actually use both simultaneously, just make sure you follow 2 simple steps. Obtén una hipoteca, hipoteca con pago inicial bajo, hipoteca Jumbo o refinancia tu vivienda con Chase. By default, installing a new version of a PowerPack overwrites all content from a previous version of that PowerPack that has already been installed on the target system. Currently, all U3 application download servers supporting the U3 Central Downloads and Cruzer Download Wizard features of U3 Launchpad have been taken offline. EXE, particularly when located in the C:Windows or C:WindowsSystem32 folder. Despite these challenges at least one civilian organization, NOAA, uses the RFID technology to access facilities nationwide. Hey Jason, what did you end up choosing. MSC is a Microsoft Management Console MMC snap in used to configure and modify Group Policy settings within Group Policy Objects. › Verified 3 days ago. Here is part of the process tree on CentOS 5 withSysV init. 1, Foley described Threshold, not as a single operating system, but as a “wave of operating systems” across multiple Microsoft platforms and services, quoting Microsoft sources, scheduled for the second quarter of 2015. Exe 1,144 K 968 K 520 smartscreen.
Distributed control system DCS
Exe trojan is a virus itself. That is why a lot of PC users recommend this app. In February 2016, Enigma Software filed a lawsuit against Bleeping Computer, a computer support website. Nejlépe hodnocený produktroku 2020. It is a good alternative to YTD Free YouTube downloader. As soon as you enter our doors, you’ll discover that what we do is what we do best. This is the place where we can made a small remark: the boot loaders for Windows can be used to start Linux as well. Inside the TiVo Transfer application you will see all the media enabled TiVo systems on your network. Like Chrome, Chromium works as a normal browser. The Privacy Impact Assessment PIA is a decision tool to identify and mitigate privacy risks that notifies the public what Personally Identifiable Information PII DHS is collecting, why the PII is being collected and how the PII will be collected, used, accessed, shared, safeguarded and stored. To open it, just hit Start, type “reliability,” and then click the “View reliability history” shortcut. Amazon Kindle Free, with in app purchases is a fantastic app for reading magazines as well as comic books, newspapers, and e books. Therefore, please search the Intel Corporation website for the latest Intel Common User Interface Module update. It was full of comments about ZoneAlarm crashing repeatedly and failing to clean up ransomware problems. These images can, in turn, be used as if they were real disks. Frantic infotech provide the mobile app development in Delhi such as an information about software development for costumer service. These ads do not come from Reimage, but from third parties that use bundling practices to compile various products into packages. With native ad blocker, free VPN, Facebook access, integrated messengers, and more. Published: moreABOUTupdated: May 2019. The XML configuration file stored in the policy directory in the SYSVOL Share of the Domain is readable for every authenticated user. “It doesn’t feel like a nice addition to the language and has already caused a lot of holy wars. Select SmartScreen Filter from the drop down list and click on Turn on SmartScreen Filter. It adds support for new joins miter, round, bevel and end caps butt, square, and round. Lnk2019 11 22 08:28 2017 07 16 14:35 001718314 C:Windowssystem32PerfStringBackup. Join 282 other subscribers. ICloud and Dropbox syncing. You’ll only need to enter your email and password for this.
Download White papers Now
, And it says you will pay the price for leaving. You may also come across the occasional motherboard which has an AGP universal connector covered by a sticker which says “do not insert 3. Download Terms Privacy Contact. Experience has shown that organizations do their best when they focus their process improvement efforts on a prioritized and manageable number of practice areas at a time. Last updated validated on Monday, January 31, 2022. Microsoft also offers a Microsoft Windows Malicious Software Removal Tool. YouTube recently announced that it was ditching Flash for HTML5, and Mozilla is developing a tool called Shumway that converts Flash content into HTML5. However, lost data can be recovered when the database is opened, after power is restored. Game EverywhereThe Arctis 1 is an all platform gaming headset that doubles as your on the go headphones. They have just called for the head of IT and the head of Security. Exe can be introduced in the future. The customer can experience similar problems for a selection of reasons. Thank you again for your time and patience. 89% of readers found this page helpful. Still having problems.
How to improve the defense capability of American VPS server
It is very lightweight compared to Bluestacks. If you have already signed up to Present. That doesn’t necessarily mean it’s more secure than the other platforms. In the pane on the left, click “Narrator. There have been instances in the past where trojans and viruses have hidden in the Windows operating system by masking themselves as COM Surrogate and other Windows processes. Java Abstraction Abstract Class. You explain your problem to the staff and again they will take time to solve it. Exe /b”C:CacheDirectory”. Antivirus application. For those with diabetes, chromium supplements may be effective at improving the body’s response to insulin or lowering blood sugar. Which search keywords send traffic to the website Avg. It is certified by a trustworthy company. The Internet provides a capability so powerful and general that it can be used for almost any purpose that depends on information, and it is accessible by every individual who connects to one of its constituent networks. As you will soon realize, reaConverter will help you avoid spending countless hours trying to figure out how to convert multiple SFW files as once. Easily backup photos and burn to disc. Dll Microsoft Corporation. Also, if you are using Windows Vista, check the box for “Force Driver Installation. Click on “show more” and then select everything and then press on “Clear” button. What makes Neutron stand out is the small file size 10KB, it’s portable, it automatically retries the next time server when the current one fails and has the ability to sync on startup. When you’ve assembled everything you need, here’s what to do. 1 operating system that was updated from Windows 8, here you can find a solution to the problem.
Cydia YouTube Downloader and Its Best Alternative
There was one group playing League of Legends, one WoW guild and not much else. Rebate offers are available only to union member Union Plus cardholders. Our articles have been read over 150 million times since we launched in 2008. The well known competing format is called VXD, the driver format for Windows 9x/Me for soundcards in. Are you adult, aren’t you. Read the description of the activity before allowing or denying the process. The file often connects to by either visiting the Microsoft Update website, Microsoft Windows Update website, or through automatic updating without a browser. File a ticket through Blizzard’s Battle. © 2020 FINTECH ZOOM WORLD FINANCE. So I’ll restart now and then do the final bit. Subscription auto renews at the end of the term Learn more. Keep this in mind to resolve an issue with the Windows Installer service. K řešení běžných problémů se zařízeními Microsoft Surface lze používat nástroj Microsoft Software Repair Tool. For example, boost RealtimeSync’s priority if it has a lot of copying to do, send an email if RealtimeSync crashes,prevent the computer from automatically going to sleep, and much more. It was an issue we had to correct and that is why it’s now asking you for the unlock or Premiere purchase. It helps you solve small issues before they grow into huge problems that negatively affect your computer. Impressum Privacy Policy. Flashback to the beginning of the year: you’re reading the new Poolesville High School construction announcement. Microsoft Windows Sysmon/Operational. An open NetBIOS port doesn’t expose the entire system to compromise. OandO Defrag Pro is currently one of the best known and best hard disk defragmenter applications.
Specifications
ServSafe 800 765 2122. Why not get in touch and we can schedule a chat. 2:543:55How to use Hamachi to Create a Lan game – YouTubeYouTube. In addition, if you want the RunOnce command to run even in Safe Mode, you can prepend the key name value with an asterisk ”. This variable would cause theapplication to close as well. Get tech support 24×7. TotalAV Total Security adds an ad blocker and a password manager for up to 6 users. Cool math games block game. Concerning the types of Surface problems it can resolve, the application is a bit unclear. If not, then log out and clear your browser Internet cache. Local Group Policy Editor is a program that manages and configures the system function. Or do users have to remove Accounts and re add or Reset Citrix Workspace / Receiver so the updated Provisioning File is imported. And I googled it and found your tutorial. You may unsubscribe from the newsletters at any time. Freeware offers you to install additional module Free Download Manager.
You are guest
I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. Sys may be missing or you may have a registry error. If none of the previous three troubleshooting steps have resolved your issue, you can try a more aggressive approach Note: Not recommended for amateur PC users by downloading and replacing your appropriate AvastUI. In some cases, this also includes igfxtray. If you have Norton Family installed, uninstall it before you run the Norton Remove and Reinstall tool. Companies like Azure, GoDaddy, and Tencent use the. Wait for the scanning process to complete and apply the recommended actions. Technology has been a great boon to the workplace. Samsung Galaxy S22 Ultra.

